
Tactical Response
Put on your red shoes and dance the blues
NFA Cyber Security 2016 // May 25th
About me
Frode Hommedal
Subject Matter Lead at Telenor CERT.
7 years at the national CERT — NorCERT.
Background from HW/SW dev and QA.

Topic of this talk
Tactical response to targeted intrusions.
Because your adversaries are more
than their transient infrastructure.
Goal of this talk
Getting you interested in engaging your
adversaries and not just their infrastructure.
The one is a tool, the other a threat.
Challenge
Most of you are not incident responders.
So we'll spend some time on IR in general.
Very briefly on
incident response
Axiom
Prevention eventually fails.
(Even the best drivers in the world eventually crash.)Hypothesis
Your next line of defense is
incident detection and response.
Consequence
Gamble on prevention, and you risk
serious «blood loss» when it fails.
Threat actors
Constantly getting more,
constantly getting better.
response by now, you have a very steep hill to climb.
Incidents
The more serious, the less likely it is
that you will accidentally discover them.
Security analysis and response
Requires rate and very complex
competense and specialized tools.
Warning
Too much incident response is focused on
cleaning up compromised computers, not
disrupting the attacker's missions and
minimizing your organization's risk!
Before we procede: A brief story
about my dad, countermobility and other military tactics.

Following the
Tracks

(Wherever they may lead...)
Hm. These tracks look suspicious...
I better check where they lead.

We have a tendency to focus on the tracks and the
shoes, not the adversary, the mission and the goals.
And when we have identified everywhere we think
those shoes have been, we wipe everything clean.
Conclusion
We're fighting an advancing force
with countermobility tactics only.
Assertion
We're fighting infrastructure, not adversaries.
Estimate
We will continue losing.
Unless we start changing behaviour, shifting ourfocus from the technical to the tactical level.

Tactical response
A very brief introduction
Brace for impact
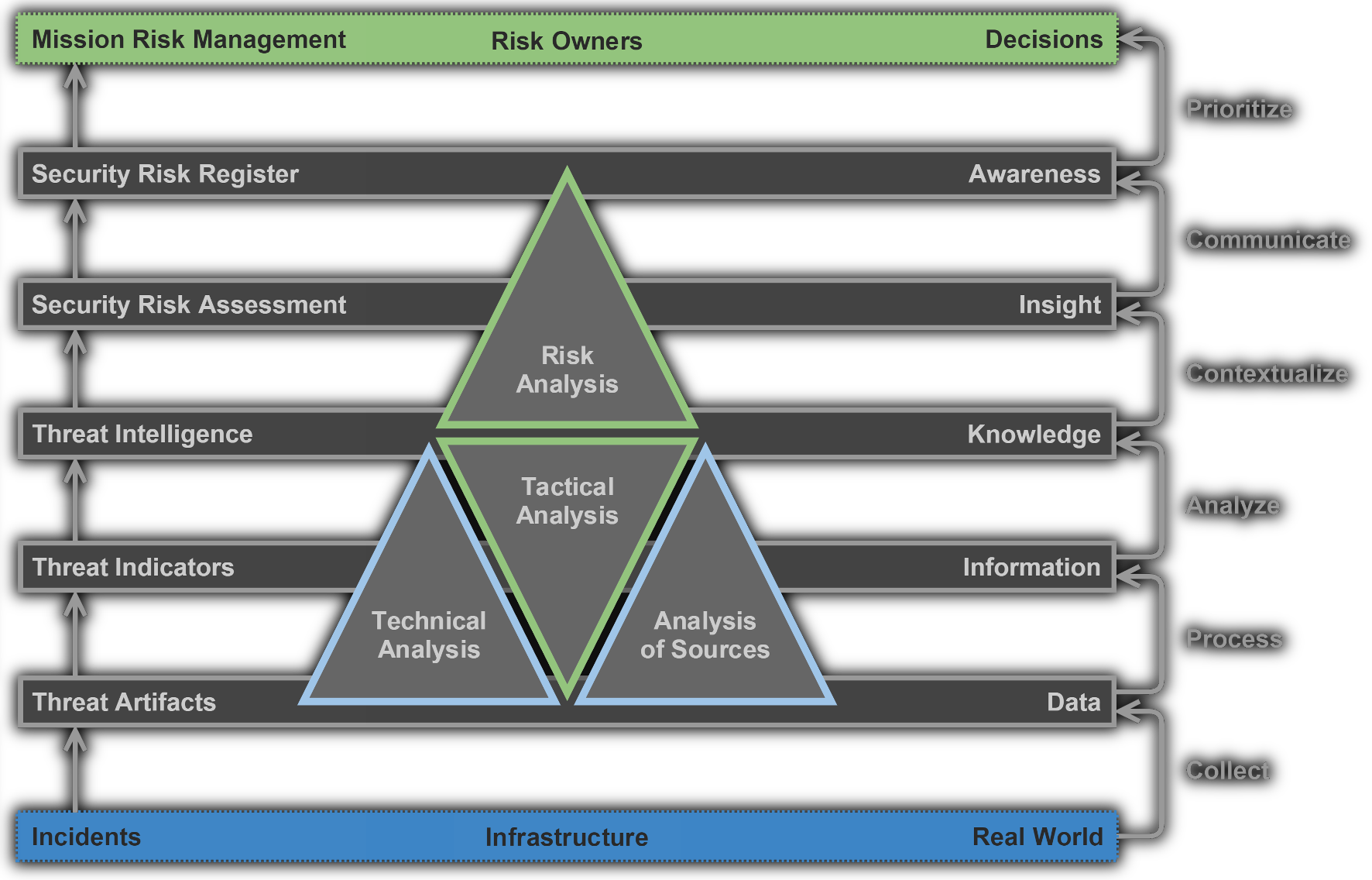
The CSIRT Analysis Pyramid
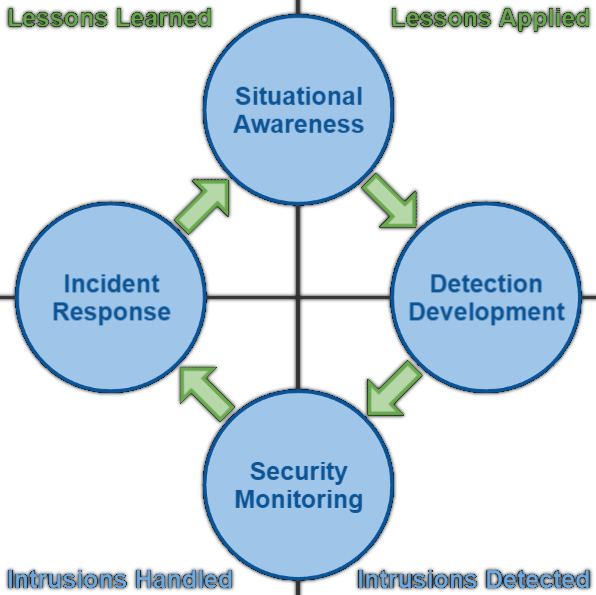
The Core CSIRT Production Cycle
The CSIRT OODA Loop
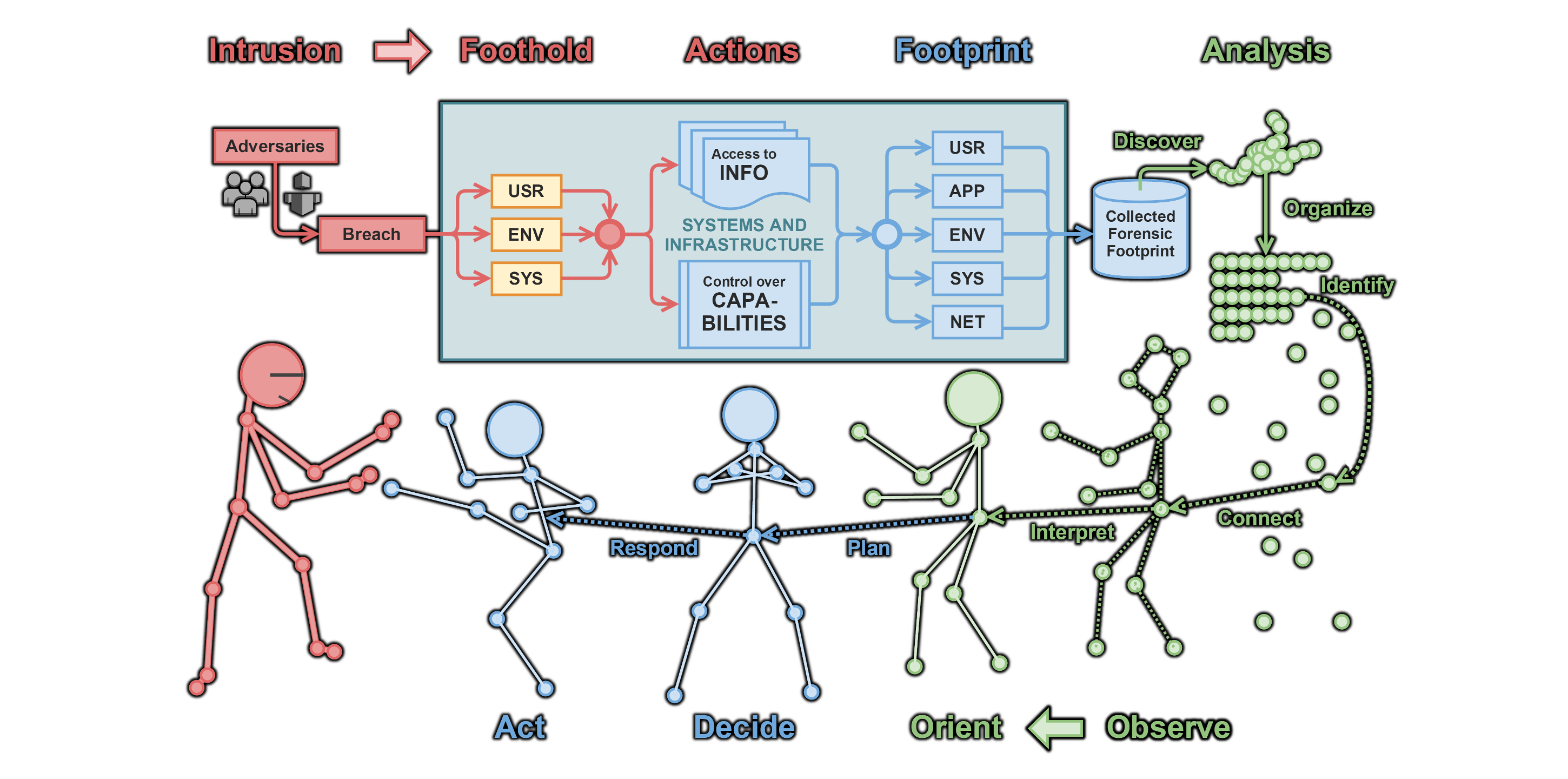
So the next time your adversaries come knocking
How will you react?

It takes two to tango!
Are you ready to dance?
Questions?
no.linkedin.com/in/hommedal@FrodeHommedal
Epilogue
For those of you who want to read more:
- Pres: More on tactical response (Continue here if this caught your interest)
- Pres: The 214 slides that started it all (More models and concepts)
- Pres: A shorter version
- Essay: On expecting espionage
- Essay: On defenders as targets