
Sikkerhetskonferansen 2016
Tactical Response
Presentation made using reveal.js. Type ? for navigation help, or just skip through using space key.
About me
Frode Hommedal
Subject Matter Lead at Telenor CERT.
7 years at the national CERT — NorCERT.
Background from HW/SW dev and QA.
I think a lot about models and methodologies.

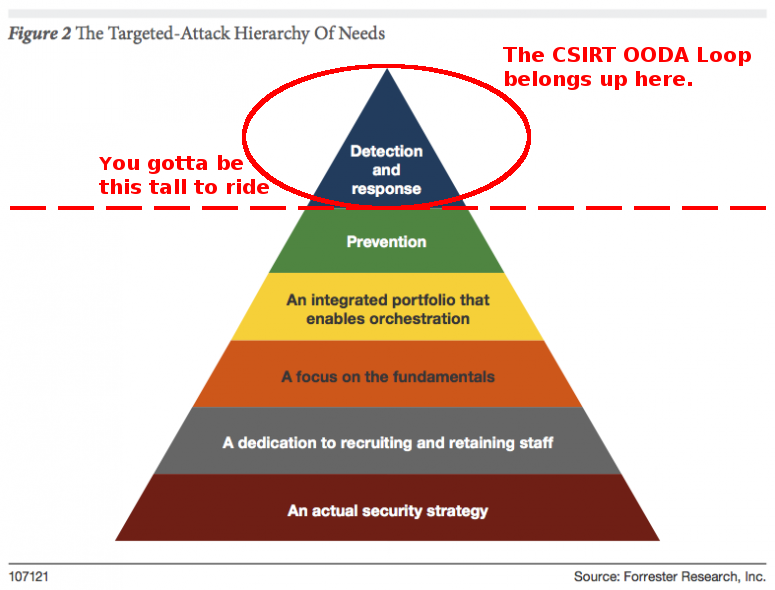
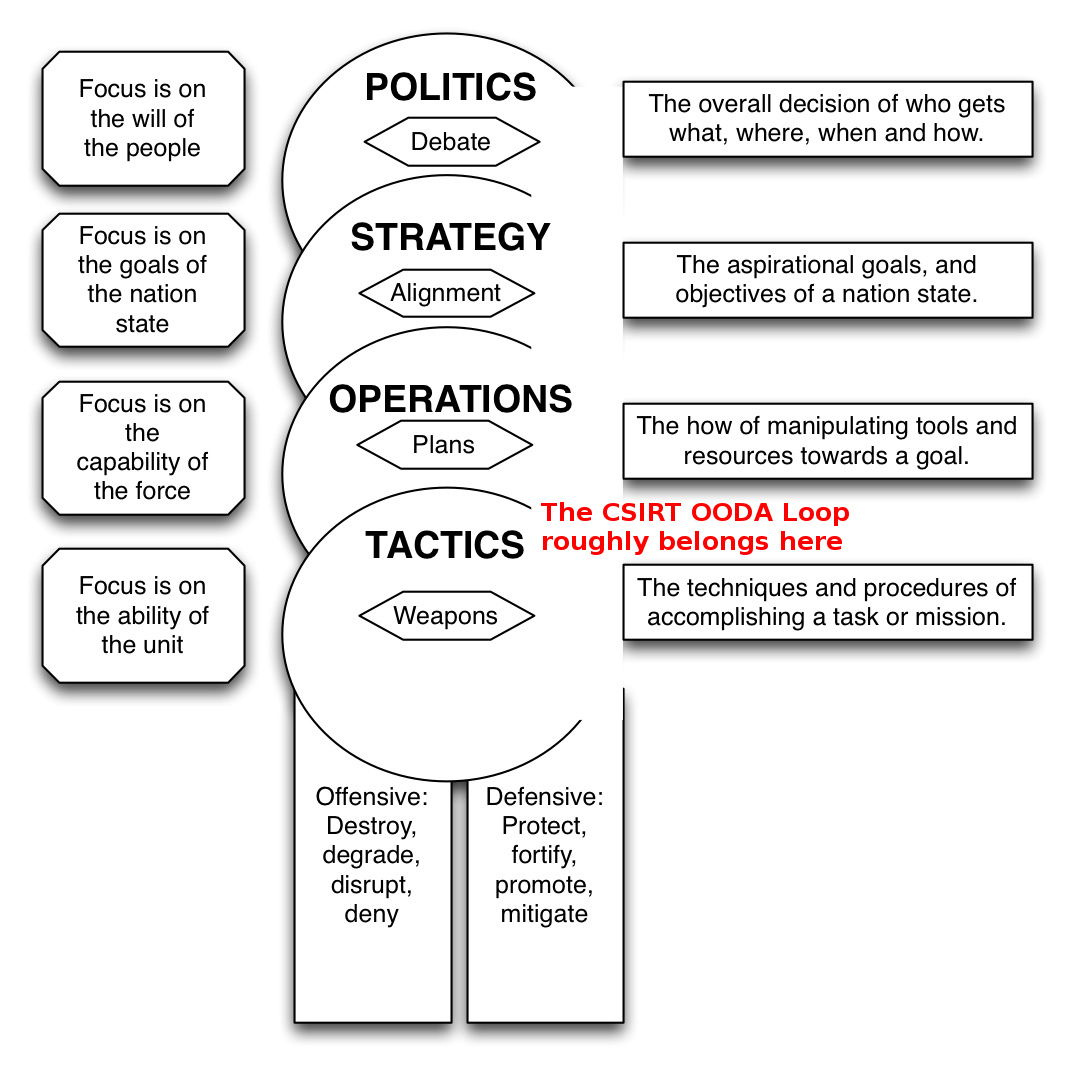
The topic of this talk
The CSIRT OODA Loop
A model to help you prepare, plan and execute your
tactical engagement of adversaries during incidents.
Why this topic?
Because we are being seriously
outperformed by our adversaries
We have actually had to conclude that we are (still) unable
to design, deploy and operate IT infrastructure securely.
How will it help?
It will sustain a more active cyber defense program
At the moment we are too often just cleaning up after cyber intrusions,
instead of trying to actively engage the adversaries as intrusions unfold.
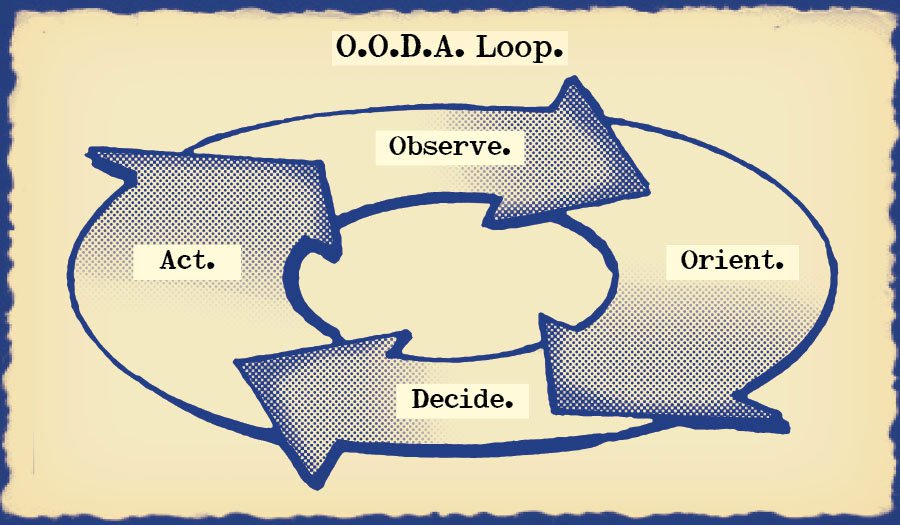
John Boyd and the OODA Loop
Taking the initiative


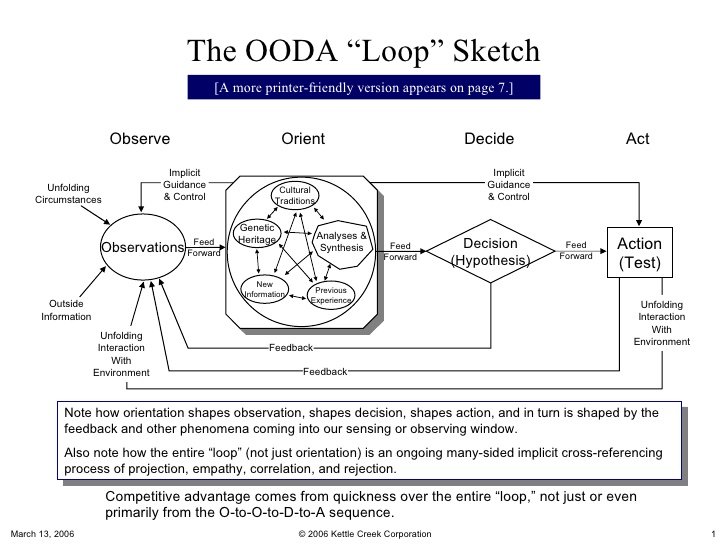
Obviously related to all decision making
Tailored for kinetic combat, but relevant for most
time constrained actions in an adversarial context.
Now let's apply it to incident response
WARNING: Brace for impact...
(Dense illustration ahead)
Engaging your adversaries with
The CSIRT OODA loop
Attackers want
accass to information and
control over capabilities
We want
to limit the risk exposure and
damage to our organizations
from our adversaries' operations
Attackers
have three main foothold perspectives
We as defenders
have five main footprint perspectives
If you can make this happen
you may eventually learn to
outperform your adversaries
</presentation>
Questions?
no.linkedin.com/in/hommedal@FrodeHommedal